The APWG report 2H2013 seeks to understand trends and their significance by quantifying the scope of the global phishing problem.
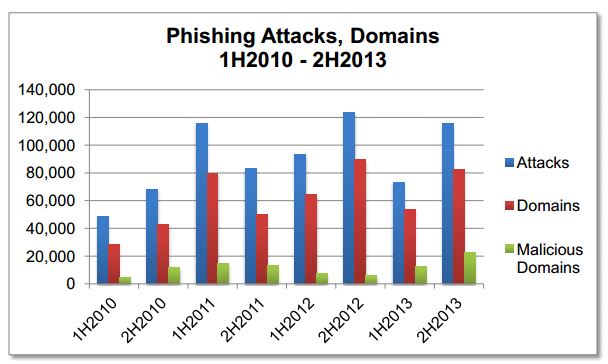
Last Anti-Phishing Working Group APWG report titled “Global Phishing Survey: Trends and Domain Name Use in 2H2013” confirms that threat of phishing has never been so high, the number of domains registered to conduct this kind of illicit activities has passed all records in the second half of 2013. Chinese phishers are the most aggressive and they were responsible for 85% of the domain names that were registered for phishing activities.
The phishing attacks are mainly suffered by Chinese online population instead better-secured US and European netizens. The overall number of malicious domains used for phishing attacks reached a total of 82,163 in the second half of 2013, 59,332 were compromised web hosts while remaining 22,831 were registrations made by phishing criminals.
The scale of phishing activities against the Chinese population during last year should worry the local authorities, for Chinese cyber criminal gangs it is very easy to register and manage domains for illicit activities without incurring in any sanction.
The APWG report states that there were at least 115,565 unique phishing attacks worldwide, an increase of 60% respect first half of 2013.
“Most of the growth in attacks came from phishing that used maliciously registered domains and subdomains. An attack is defined as a phishing site that targets a specific brand or entity. A single domain name can host several discrete phishing attacks against different banks” states the APWG report.
Another interesting aspect related to phishing attacks occurred in the H2 2013 is that the average uptimes of phishing attacks is declined respect the first part of the year, the average duration was 28 hours and 43 minutes, while the median uptime was 7 hours and 54 minutes. The data confirm that phishing attacks must succeed quickly, half of all the offensives stay active for less than 8 hours.
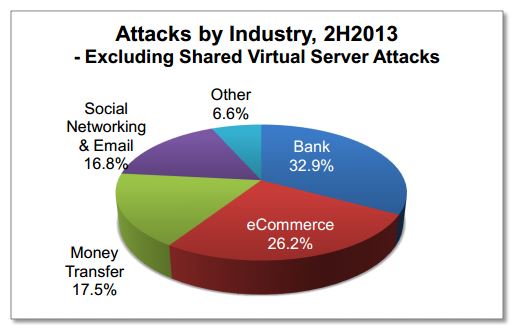
Very interesting is the data related to target distribution, the APWG report discovered 681 unique phished target institutions (mainly financial and ecommerce), 324 of them were totally new and not attacked in the first part of the year, this means thatphishers are trying out new targets.
“They appear to be looking for companies that are newly popular, have vulnerable user bases, and/or are not ready to defend themselves against phishing” states APWG report.
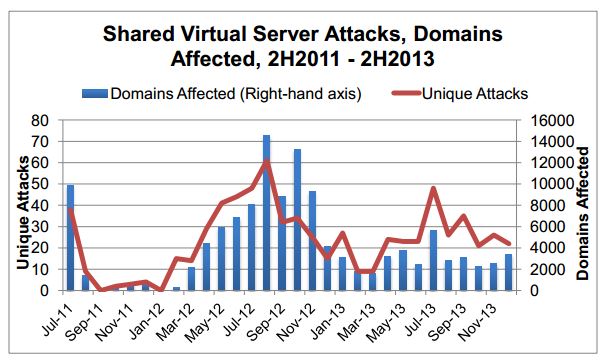
As occurred already in the past, phishers continue to break into web servers that hosts a large number of domains, “shared virtual servers”, in this way just updating server configuration with malicious content the hackers can compromise multiple domains.
“Instead of hacking sites one at a time, the phisher often infects hundreds of web sites at a time, depending on the server. In 2H2013, we identified 178 mass break-ins of this type, resulting in 20,911 phishing attacks. This represents 18% of all phishing attacks recorded worldwide”
The APWG report definitely suggests that phishing is changing, phishers are exploring new tactics and they are searching for new targets. We must consider that China isn’t the unique country to suffer phishing activities, US for example suffer a much bigger problem related to small-scale spear phishing attacks, which are not analyzed by the APWG because they are targeting single enterprises and can’t be detected through domain registrations.
As explained in the APWG report spear-phishing continues to be an important tool for:
- Criminals who are perpetrating financial crimes against specialized or small targets, like students at a particular university.
- Spies involved in corporate and government espionage.
- Hacktivists who seek publicity for their causes.
No comments:
Post a Comment